Ports & Protocols
October 31, 2025
Netlas uses its own scanning technology, purpose-built for safe, high-speed, and large-scale internet scanning. We constantly improve both our scanning infrastructure and the scanners themselves to expand coverage and decreace time of scanning cycle.
IP and Port Coverage
Netlas scans the entire IPv4 space against a curated list of commonly used ports, which periodically expands in proportion to our infrastructure growth.
| Coverage | Details |
|---|---|
| IPv4 Space | Entire IPv4 space — from 1.0.0.0 to 239.255.255.255. Reserved and special-use ranges are excluded. |
| IPv6 Space | Currently, the IPv6 is not supported for scanning. |
| TCP Ports | 11, 13, 15, 17, 19, 21, 22, 23, 25, 26, 37, 43, 49, 53, 70, 79, 80, 81, 82, 83, 84, 85, 88, 90, 93, 97, 102, 104, 106, 110, 111, 113, 119, 122, 135, 137, 139, 143, 175, 179, 189, 190, 192, 195, 199, 221, 264, 285, 311, 314, 389, 400, 427, 440, 441, 443, 444, 445, 465, 480, 500, 502, 503, 513, 515, 541, 548, 554, 556, 587, 593, 631, 636, 646, 666, 771, 785, 789, 808, 809, 811, 843, 853, 873, 886, 887, 888, 902, 953, 990, 992, 993, 995, 1000, 1002, 1023, 1024, 1025, 1026, 1027, 1028, 1029, 1080, 1099, 1110, 1111, 1153, 1177, 1180, 1194, 1200, 1207, 1234, 1311, 1337, 1344, 1400, 1414, 1433, 1443, 1447, 1471, 1515, 1521, 1599, 1604, 1605, 1701, 1723, 1741, 1800, 1801, 1883, 1900, 1911, 1925, 1926, 1935, 1958, 1962, 1965, 1966, 1970, 1980, 2000, 2001, 2002, 2003, 2008, 2012, 2022, 2031, 2049, 2052, 2053, 2067, 2077, 2079, 2081, 2082, 2083, 2086, 2087, 2095, 2096, 2100, 2103, 2107, 2121, 2154, 2181, 2200, 2222, 2271, 2323, 2332, 2345, 2375, 2376, 2379, 2404, 2423, 2443, 2455, 2480, 2525, 2599, 2628, 2761, 2762, 2850, 3000, 3001, 3050, 3128, 3160, 3165, 3260, 3268, 3269, 3299, 3301, 3306, 3307, 3310, 3333, 3341, 3388, 3389, 3443, 3460, 3510, 3531, 3541, 3542, 3551, 3580, 3590, 3689, 3702, 3749, 3780, 3790, 4000, 4010, 4022, 4040, 4063, 4064, 4085, 4100, 4150, 4157, 4165, 4190, 4242, 4244, 4282, 4321, 4343, 4344, 4369, 4401, 4430, 4433, 4434, 4443, 4444, 4445, 4447, 4449, 4461, 4477, 4500, 4502, 4506, 4567, 4572, 4664, 4782, 4786, 4840, 4848, 4899, 4911, 4949, 5000, 5001, 5003, 5005, 5006, 5007, 5009, 5010, 5025, 5060, 5061, 5083, 5090, 5100, 5105, 5120, 5130, 5135, 5150, 5160, 5190, 5201, 5222, 5225, 5226, 5227, 5229, 5231, 5234, 5235, 5236, 5237, 5240, 5242, 5244, 5245, 5246, 5248, 5249, 5251, 5252, 5255, 5256, 5269, 5271, 5272, 5277, 5357, 5432, 5433, 5435, 5440, 5443, 5446, 5503, 5544, 5555, 5560, 5601, 5620, 5640, 5658, 5671, 5672, 5680, 5683, 5701, 5800, 5801, 5804, 5858, 5900, 5901, 5902, 5903, 5904, 5905, 5906, 5907, 5908, 5909, 5910, 5911, 5914, 5915, 5916, 5917, 5918, 5920, 5938, 5984, 5985, 5986, 5989, 5991, 5995, 5997, 5998, 6000, 6001, 6002, 6006, 6007, 6020, 6036, 6050, 6060, 6061, 6066, 6080, 6100, 6264, 6379, 6380, 6440, 6443, 6482, 6501, 6606, 6633, 6653, 6664, 6666, 6667, 6668, 6686, 6688, 6697, 6699, 6881, 7000, 7001, 7002, 7005, 7007, 7010, 7013, 7014, 7020, 7022, 7025, 7050, 7070, 7071, 7078, 7079, 7080, 7081, 7082, 7083, 7084, 7085, 7086, 7087, 7088, 7100, 7102, 7105, 7170, 7171, 7218, 7272, 7403, 7415, 7434, 7443, 7474, 7510, 7547, 7548, 7634, 7657, 7676, 7707, 7771, 7773, 7775, 7777, 7778, 7779, 7900, 7979, 7989, 7999, 8000, 8001, 8002, 8003, 8004, 8005, 8006, 8008, 8009, 8010, 8011, 8015, 8020, 8022, 8023, 8026, 8058, 8060, 8061, 8069, 8080, 8081, 8082, 8083, 8084, 8085, 8086, 8087, 8088, 8089, 8090, 8091, 8092, 8093, 8096, 8098, 8099, 8100, 8102, 8104, 8105, 8109, 8110, 8112, 8113, 8123, 8126, 8139, 8140, 8159, 8181, 8188, 8190, 8200, 8203, 8222, 8291, 8300, 8333, 8334, 8343, 8383, 8440, 8441, 8443, 8444, 8445, 8449, 8451, 8453, 8454, 8455, 8500, 8502, 8503, 8506, 8513, 8520, 8521, 8525, 8528, 8529, 8536, 8543, 8544, 8545, 8549, 8554, 8556, 8562, 8566, 8570, 8573, 8575, 8576, 8578, 8581, 8591, 8593, 8594, 8599, 8602, 8606, 8649, 8686, 8702, 8703, 8704, 8705, 8708, 8709, 8728, 8731, 8732, 8764, 8800, 8808, 8834, 8880, 8885, 8886, 8887, 8888, 8889, 8899, 8999, 9000, 9001, 9002, 9003, 9004, 9009, 9013, 9042, 9051, 9052, 9053, 9054, 9055, 9056, 9057, 9061, 9062, 9063, 9064, 9065, 9066, 9068, 9069, 9072, 9073, 9074, 9075, 9076, 9077, 9080, 9082, 9087, 9089, 9090, 9091, 9092, 9095, 9098, 9100, 9112, 9113, 9114, 9115, 9116, 9117, 9118, 9119, 9120, 9121, 9122, 9123, 9124, 9125, 9128, 9134, 9140, 9141, 9142, 9143, 9144, 9145, 9146, 9147, 9148, 9149, 9150, 9151, 9152, 9153, 9157, 9158, 9159, 9160, 9161, 9162, 9163, 9164, 9165, 9166, 9167, 9168, 9169, 9170, 9172, 9174, 9175, 9176, 9177, 9178, 9179, 9180, 9181, 9182, 9183, 9184, 9185, 9186, 9187, 9188, 9190, 9191, 9192, 9193, 9195, 9196, 9197, 9198, 9200, 9243, 9289, 9295, 9306, 9333, 9350, 9387, 9398, 9410, 9418, 9441, 9443, 9445, 9454, 9455, 9456, 9501, 9510, 9530, 9532, 9595, 9600, 9633, 9674, 9710, 9711, 9734, 9754, 9761, 9773, 9779, 9800, 9803, 9804, 9869, 9876, 9898, 9901, 9943, 9944, 9966, 9981, 9988, 9998, 9999, 10000, 10001, 10002, 10003, 10004, 10005, 10006, 10007, 10008, 10009, 10013, 10020, 10022, 10050, 10051, 10065, 10075, 10080, 10081, 10100, 10134, 10225, 10243, 10250, 10324, 10380, 10443, 10533, 10554, 10892, 10909, 10911, 10934, 10935, 10936, 11000, 11002, 11007, 11101, 11110, 11112, 11180, 11210, 11211, 11288, 11300, 11371, 11401, 11434, 11601, 11602, 11680, 11681, 11701, 12000, 12111, 12323, 12324, 12325, 12326, 12345, 12443, 13579, 14101, 14130, 14147, 14265, 14344, 14401, 14402, 14403, 14404, 14406, 14407, 14873, 14875, 14880, 14894, 14895, 14896, 14897, 14900, 14901, 14903, 14905, 14909, 15000, 15001, 15018, 15038, 15040, 15042, 15044, 15123, 15151, 15443, 15588, 15831, 16010, 16030, 16316, 16800, 16831, 16992, 16993, 17443, 18080, 18081, 18245, 18264, 18443, 19000, 19015, 19071, 19233, 20000, 20001, 20010, 20018, 20020, 20030, 20040, 20050, 20060, 20070, 20080, 20090, 20100, 20106, 20107, 20121, 20200, 20201, 20208, 20256, 20500, 20512, 20547, 20600, 20880, 21001, 21002, 21025, 21200, 21242, 21300, 21305, 21379, 22000, 22022, 22103, 22107, 22206, 22222, 22556, 22705, 23023, 23424, 24442, 24808, 25000, 25001, 25002, 25006, 25007, 25105, 25565, 27015, 27017, 28015, 28017, 29840, 29842, 29984, 30000, 30001, 30002, 30003, 30005, 30006, 30050, 30104, 30106, 30110, 30111, 30112, 30113, 30120, 30121, 30122, 30123, 30443, 31337, 31444, 32080, 32101, 32102, 32303, 32400, 32764, 33060, 35000, 37215, 37777, 38520, 40000, 40056, 40443, 40894, 41337, 41800, 42901, 44158, 44303, 44304, 44305, 44306, 44310, 44333, 44336, 44345, 44350, 44444, 44818, 45000, 45001, 47001, 47990, 49152, 49153, 49501, 49502, 49592, 49682, 49684, 49686, 49688, 49692, 49767, 50000, 50001, 50011, 50012, 50050, 50070, 50100, 50101, 50113, 50443, 50805, 50995, 50996, 50997, 50999, 51000, 51001, 51002, 51003, 51005, 51007, 51106, 51235, 52230, 52311, 52869, 52881, 52931, 52951, 54138, 55000, 55442, 55443, 55553, 55554, 55555, 56001, 58000, 58603, 60000, 60001, 60010, 60030, 60129, 60443, 61234, 61613, 61616, 61617, 62078, 62237, 62865, 63260, 64295. |
| UDP Ports | 53, 123, 137, 161, 162. |
Protocol Support
Netlas identifies and parses responses for approximately 30 application-layer protocols:
| Protocol | Description |
|---|---|
amqp |
Advanced Message Queuing Protocol used for reliable messaging in IoT, cloud, and enterprise systems. |
dns |
Domain Name System protocoll, with support for both UDP and TCP transport. |
elasticsearch |
Elasticsearch RESTful engine for searching, analyzing, and managing data in real time. |
ftp |
File Transfer Protocol. |
http |
Hypertext Transfer Protocol. |
imap |
Internet Message Access Protocol allowing clients to retrieve and manage email messages. |
memcached |
Memcached protocol for high-performance distributed memory caching. |
mongodb |
MongoDB Protocol for document-based NoSQL databases. |
modbus |
Modbus industrial protocol widely used in SCADA and automation systems. |
mqtt |
MQTT, a lightweight publish-subscribe messaging protocol ideal for IoT. |
mssql |
Microsoft SQL Server Protocol. |
mysql |
MySQL Protocol. |
netbios |
NetBIOS protocol suite for basic networking services on local networks. |
ntp |
Network Time Protocol used for clock synchronization across networks. |
oracle |
Oracle Database Protocol. |
pop3 |
Post Office Protocol v3 used by email clients to retrieve messages from servers. |
postgres |
PostgreSQL Protocol. |
rdp |
Remote Desktop Protocol used for remote access to Windows desktops. |
redis |
Redis Protocol for in-memory data structure storage and caching. |
s7 |
S7 Protocol for communication with Siemens PLCs in industrial networks. |
smb |
Server Message Block protocol for network file and resource sharing. |
smtp |
Simple Mail Transfer Protocol for sending emails across networks. |
snmp |
Simple Network Management Protocol used for monitoring and managing network devices. |
socks |
SOCKS proxy protocol, used to detect and identify proxy servers. |
ssh |
Secure Shell protocol. |
t3 |
T3 Protocol, proprietary WebLogic protocol for Java EE communication. |
telnet |
Telnet protocol. |
vnc |
Virtual Network Computing protocol for graphical desktop sharing over a network. |
If the Netlas scanner cannot identify the protocol, the unparsed network response is stored in the raw_tcp field.
Extended HTTP Support
Beyond basic banner grabbing, Netlas captures full page responses, follows redirects, identifies virtual hosts, parses headers, stores favicons, and enables flexible search across collected HTTP data.
Virtual Hosts
To effectively gather data from web servers, Netlas scanners query them not only by IP address but also by domain names. If multiple websites or web applications are hosted on the same web server, Netlas will query them one after another.
Domain name-based queries are performed only on standard web ports 80 (HTTP) and 443 (HTTPS). For all other ports, Netlas scanners send requests directly by IP address without using domain names.
Virtual sites scan limit
Due to resource restrictions, Netlas scanners limit the number of virtual sites per IP to 100,000.
Because of this limitation, some websites hosted on popular hostings may not be in the search results.
HTTP Redirects
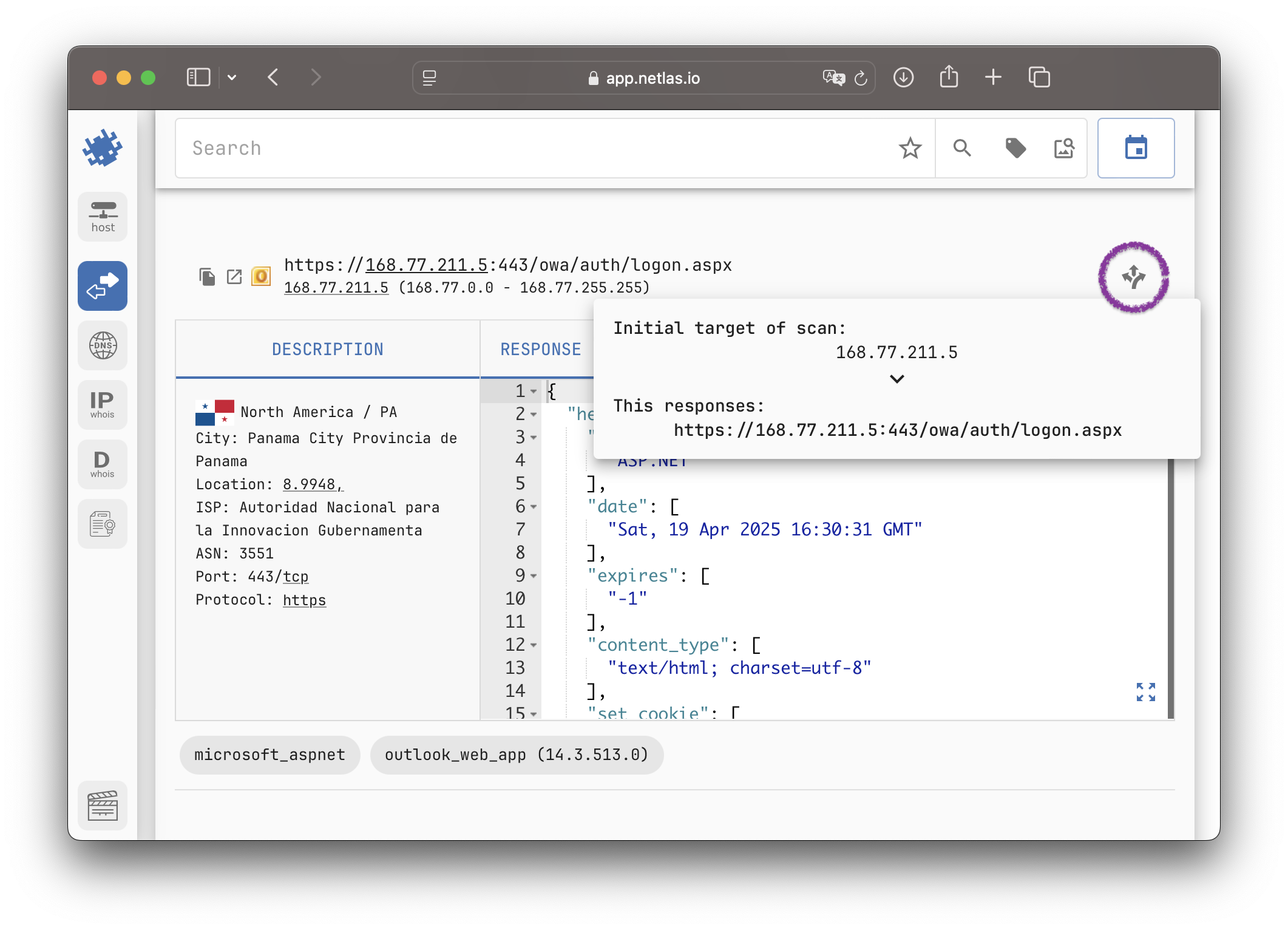
Many web servers make redirections to another address. They use special HTTP responses with codes 301 (Moved Permanently), 302 (Moved Temporarily) and some others.
Netlas scanners follow up to 5 HTTP redirects in a row. During this process, each response is saved as a separate document. Those responses differ in fields host, target, http.status_code and referer (not a typo — the word 'referer' is spelled this way in the original HTTP specification).
JavaScript
Netlas does not execute JavaScript when scanning websites.
Netlas scanners also do not follow JavaScript-based redirects — only standard HTTP 301/302 redirects are recognized and handled.
HTTP Body
Netlas parses and saves the first 100Kbytes of each response during the scan. In the vast majority of cases, this is enough to save a full server response.
HTML pages are stored in the http.body field. A full-text search is available for this field. So it is possible to search across the entire body of a web page.
HTTP Headers
HTTP headers are available in two fields: http.headers and http.unknown_headers.
The http.headers field points to 1000 of the most used HTTP headers. Other headers are stored as key-value pairs in the unknown_headers field.
All - (dashes) in header names are replaced with the _ due to database limitation
For example, use http.headers.content_security_policy instead of http.headers.content-security-policy.
Favicon Search
Netlas supports searching for websites based on favicon hashes, using two types of fingerprints:
- SHA-256 hash in the
http.favicon.hash_sha256field for exact search. - Perceptual hash in the
http.favicon.perceptual_hashfield for average search. (1)
-
How Perceptual Hash Search Works
Perceptual hashes represent the visual structure of a favicon. The greater the differences between two images, the more their hashes will differ, especially toward the end.
When searching:
- Use the full hash for an exact perceptual match.
- Trim the end of the hash and add a
*wildcard to perform partial matching and find favicons that are visually similar. - Alternatively, use the
~operator to perform fuzzy matching based on Hamming distance (1–2 symbol differences).
This flexibility helps discover related servers, clones, phishing sites, or malware infrastructure that use similar branding.
In the Responses Search tool, click the Favicon Search button on the right side of the search panel to upload a favicon.
What perceptual hashing algorithm does Netlas use?
Netlas uses the Average Hash (aHash) algorithm — a 64-bit visual fingerprint, tolerant to minor modifications like resizing, slight color changes, or compression artifacts.
📚 To dive deeper into perceptual hashing, read Dr. Neal Krawetz’s classic article explaining the principles behind aHash and other perceptual hash techniques.
SSL/TLS Support
Netlas supports identification and parsing of secure versions of common protocols, including HTTPS, FTPS, IMAPS, SMTPS, POP3S, and STARTTLS-enabled services.
Whenever a secure connection is detected, we always extract and store the server's X.509 certificate.
Sometimes, an SSL/TLS certificate is the only information available from a service.
Indicatiors of Malware Infrastructure
This often happens with malware-related servers, which are configured not to respond to any unauthenticated requests — providing no banners, headers, or service responses until proper authorization is completed.
In such cases, the collected certificate becomes the primary and the only indicator of the service's existence.
JARM Fingerprints
Netlas supports JARM — a TLS server fingerprinting technique developed by Salesforce for identifying and grouping servers based on their TLS configurations.
JARM is a method for fingerprinting TLS servers based on the way they respond to a set of 10 specially crafted TLS Client Hello packets. JARM fingerprints are stored in the jarm field.
Currently, Netlas generates JARM fingerprints only for HTTPS services. If the target server does not respond over HTTPS or uses a non-standard TLS configuration, a JARM fingerprint may not be available.
Extended RDP Support
In addition to detecting RDP services, Netlas collects the following:
- NetBIOS Information: Key system identifiers such as computer name, domain name, OS version, and server time.
- Desktop Screenshots: After establishing a connection, Netlas captures a screenshot of the RDP login screen or desktop.
- OCR (Optical Character Recognition): Netlas automatically extracts and indexes visible text from RDP screenshots, allowing users to perform full-text search across recognized screen contents.
Use rdp.text field to access recognized screen contents.